The dark side of the Internet of Everything


Connecting state and local government leaders
The simple act of turning on your cell phone exposes you to being tracked across the Internet – even if you have switched off location-based services.
We’re all learning about the dangers of big data. You buy something on Amazon and suddenly all your contacts know about your purchase.
Now it turns out that the simple act of turning on your cell phone exposes you to being tracked across the Internet – even if you have switched off location-based services.
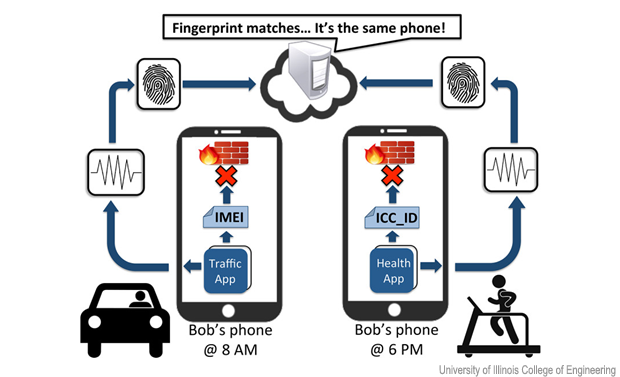
Researchers at the University of Illinois’ College of Engineering have discovered that, due to imperfections in manufacturing processes, cell phone sensors have unique characteristics that can be used to identify the phone.
If, for example, you’re driving to the gym and use your phone to access check on traffic, that app reads data from the phone’s accelerometer. When you arrive at the gym, data from the accelerometer is also used by an application on the treadmill that measures your gait and distance traveled. If those two transmissions of accelerometer sensor data are compared, an analyst can determine that they came from the same phone.
In short, your cell phone transmits data as you move through the digital universe, leaving “fingerprints” that give information not only about your location but about your activities.
While the researchers at the University of Illinois focused on accelerometer data, they say there’s no reason to believe other sensors in phones – gyroscopes, microphones, proximity sensors, pressure sensors, cameras, etc. – don’t leave similar fingerprints. So the potential is there to link, identify and track an incredible amount of activity.
What’s more, says principal researcher Nuripam Roy, the degree of expertise required to tap into this data is not very high.
“Anybody with a little knowledge of statistics and a little knowledge of computer science can do it,” Roy said. “As it can be done pretty easily, it’s a big concern.”
That’s especially true since laws and regulations haven’t kept up with the technologies. “There is no regulation, no need to get permission to approach this kind of data,” Roy said. “What we have shown is that this apparently benign-looking data can be as good as sharing the MIN [mobile identification number] number of a phone.”
The team tried to find ways to mask the identifying characteristics, without success. “We couldn't find any reasonable way to wipe this off the sensor data,” Roy said. “We need to keep in mind that the sensor data has functionality, so we can't process it too much or may become useless for the application.”
Roy added that there may be some ways to take advantage of the sensor fingerprints, such as using cell phones as identity cards. But doing so in a secure way requires more research.
In the meantime, he said, manufacturers – and governments that regulate them – may want to consider the implications. “We think that these idiosyncrasies in the sensors are coming from the factory production line,” Roy said. “It may be that there will be more concern about those processes.”
Can the manufacturing processes be changed to eliminate the fingerprints? “We need more research,” Roy said.
NEXT STORY: The 1776 crew marches into FOSE




