VA gets its rights
Case study: Department specifies how people can use ' or not use ' documents employees create.
The Veterans Affairs Department has certainly taken its lumps over data loss in the past few years. In 2006, a VA employee took home records of more than 26 millions veterans on a laptop PC, which was subsequently stolen.
So, to say that Charlie De Sanno, executive director at VA's Office of Enterprise Infrastructure Engineering, has data security high on his list of priorities would be an understatement.
Perhaps not surprisingly, VA has become one of the earliest adopters ' and thus far, the largest ' of rights management software with its use of Microsoft's Rights Management Services (RMS).
VA expected that by press time all employees would be able to set restrictions on what can be done with the documents they create.
When Word, PowerPoint or Excel files, or Outlook e-mail messages are sent to others, the authors can set permissions on what the recipients can do with those documents.
The creator of the document can decide whether it can be printed, forwarded or edited by other people. It's the employee's or the agency's call.
Moreover, the documents are encrypted, so anyone without the appropriate permissions cannot see the contents.
'This ability provides our agency and users the assurance that only the author of the content or someone that has been given full-control permission to the content can remove the persistent protection from the e-mails and documents,' De Sanno said.
'For instance, say I send you an e-mail and RMS that message,' De Sanno said. 'I can actually say you cannot print this [document], or that you cannot forward this. Or, it can evaporate in 30 days.'
Among employees, contractors and other people, more than 250,000 individuals will shortly begin using this feature, the agency said.
Rights management will be extended to users other than VA employees and will work with the agency's BlackBerry and Windows mobile clients.
Last year, VA Chief Information Officer Bob Howard decided to apply rights permissions to all of VA's private patient health information as quickly as possible. De Sanno's team gave itself and lead integrator IBM a 90-day deadline to complete the project.
The agency already had a head start. It has been deploying public-key infrastructure for a while to encrypt sensitive documents. PKI had its limits, though.
With PKI, 'you can only ensure that the e-mail is encrypted in its transmission end-to-end, but once the recipient opens the PKI e-mail, they can do whatever they want with the message and/or attachments,' De Sanno said.
RMS would allow the agency to specify what the recipients could do with the documents.
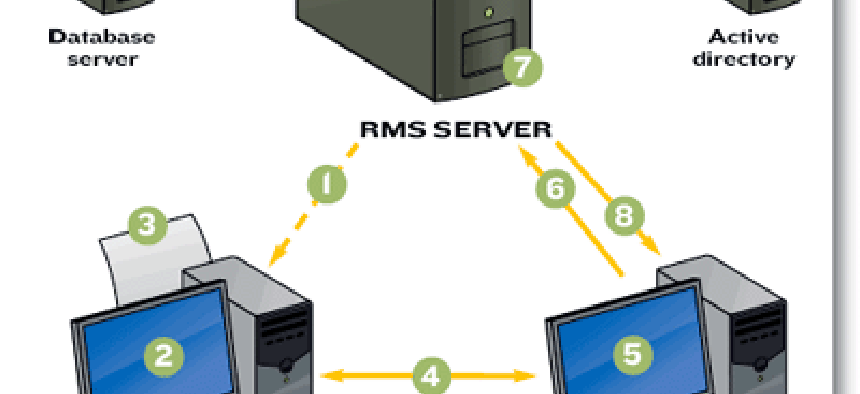
With RMS, a central server ' or, in VA's case, six servers ' keeps tabs on the rights assigned to each document. Each employee gets a client certificate from an RMS server, which identifies that individual.
If someone chooses to set permissions on a document, that individual's copy of Microsoft Office sends the permissions for that document to RMS, along with the digital certificate.
VA has a set of forms in place that employees use to set the parameters.
VA's copies of Microsoft Office can also set global usage policies for specific types of documents or set policies that are relevant to an office or job function. The department used RMS' message classification feature to secure content based on policies set in Active Directory.
That would help users decide if what they are sending should be considered sensitive data that needs protection, De Sanno said.
'You can pretty much define policy for anything you do with information,' said John Chirapurath, director of identity and access product management at Microsoft. For instance, a top-secret tag could be applied to all sensitive documents.
RMS also issues keys to the recipients to open the documents. When a recipient receives a document from a VA employee, the program sends the request to the RMS server, along with the key. RMS responds with a list of rights the individual has with that document.
The document remains encrypted until RMS grants permission to open it.
Although this is a complicated dance between the servers and the client software, the whole transaction is transparent to the user, Chirapurath said.
To take advantage of RMS, all participating parties must use Microsoft Office 2003 or 2007. Microsoft also has published the Windows Rights Management Application Programming Interfaces, which would allow third-party software providers to have their programs interact with RMS. The application runs on Windows Server 2003 and the soon-to-be-released Windows Server 2008.
Although it looks simple enough on paper, getting a proper RMS running for more than 250,000 people required some planning, De Sanno said. The team came up with 240 line items for requirements for the job.
Ready for backup
To guarantee reliability, the RMS system had to be fault-tolerant. VA needed to install and test a live, readily functional backup system.
'In the event of a failure, we will be able to service the entire nation out of one site until the redundant site is brought back online,' De Sanno said.
'We desired our systems' failover to be completely automatic in 60 seconds or less,' he said.
In VA's setup, two locations each have a set of three RMS servers. They split the work, through load-balancing, courtesy of Cisco load balancer and Cisco Global Site Selector appliances and appliances. When one location goes down, the other is designed to handle the entire workload.
A server at a third location pings the redundant RMS servers whenever downtime occurs to ensure that they are running.
To keep the records at both locations as similar as possible, VA uses Microsoft SQL Server 2005's mirroring function. This approach works better than backing up from one storage-area network to another, De Sanno said. 'SAN to SAN is good but requires fancy scripting and in some cases manual failover,' he said.
VA employees using RMS are identified through the department's Active Directory implementations. To handle individuals not in VA's Active Directory ' such as doctors at outside hospitals ' VA deploys proxy server software, GigaTrust Enterprise, from GigaTrust. This software lets users set up accounts that can then interact with VA's RMS. VA doesn't have to add these users to its own Active Directory for RMS to recognize them, said Lesley Gorog Harris, GigaTrust public sector vice president.
Fast storage
For storage, the agency deployed an 8T SAN, arranged in Redundant Array of Independent Disks 10 configuration, the version of Redundant Array of Independent Disks optimized for high-performance reading and writing. 'Now that we have RAID 10 we will be reading and writing the data as fast as the SAN, with its fiber connection, is capable,' De Sanno said.
An LTO 3 tape backup system was put in place to back up the entire dataset ' about 6T worth ' in about 14 hours.
The blade servers, supplied by IBM, boot directly from the SAN.
'Booting from SAN will help us in the future if a blade server needs to be replaced because the server identity stays with the boot disk and not with the blade that failed,' De Sanno said.
Microsoft Operations Manager monitors daily operations of the RMS system now, and the agency will soon start using Systems Center Operations Manager 2007, too.
Going mobile
One of the more complicated pieces of the puzzle was how to include traveling VA employees who use their handheld units to read, write and forward documents. Although Microsoft supports RMS for Windows Mobile 6 clients, the department contracted GigaTrust to provide software to enable BlackBerrys to work with RMS, and it chose Trust Digital for older Windows Mobile platforms.
'After the data breach, we really strengthened our security controls,' De Sanno said. 'VA wanted to ensure that data anywhere on mobile devices was encrypted.' The last thing VA executives want is for a mobile device to be lost and outsiders to be able to read its contents. RMS, along with the mandate for users to deploy really strong passwords, helps in this regard.
Handheld protection
For instance, VA has about 7,500 devices in operation. The department is deploying GigaTrust for BlackBerry to add the RMS permissions to these devices. The software is installed on each BlackBerry.
'It's very intuitive,' Harris said. 'There is very little required. The first time the user loads the thin client, it's much like the Adobe client.'
GigaTrust's software can also monitor Black- Berry users to help ensure they do not send sensitive information.
For instance, the department can set up regular expressions to monitor outgoing messages for sensitive information, such as Social Security numbers.
For VA, specifying how data is used goes a long way toward keeping that data secured.
'RMS provides the VA with more granular control of documents,' De Sanno said. And that can do a lot to prevent future losses of data.

2.
3.
4.
5.
6.
7.
8.
NEXT STORY: SCAP narrows security gap





