Cipher provides an easy way to secure USB drives

The Cipher USB FLE from Addonics, which itself looks like a key drive, can encrypt files on any drive or host PC.
Government has a love/hate relationship with key drives. Agency workers, just like everyone else, love the convenience of being able to store gigabytes of information in the palm of their hands. But if those little devices are lost or stolen, it means a lot of data is potentially compromised.
And given how cheap storage media is these days, even the average user is likely to collect a handful of key drives. Some of those devices are likely to have pretty large storage capacities, but you still can’t use them at the office. But what if you could somehow “secure” those key drives in your desk drawer?
The Cipher USB FLE F1 from Addonics Technologies, claims to be able to take any generic key drive and make it secure enough for government use. It sounded like a bit of a magic trick, so we were happy to pull back the curtains to see how, and how well, such a device actually worked.
The Cipher USB FLE is inexpensive, at $40, and looks like a key drive itself. It plugs into a USB port and has another port on the back where you can attach the drives you want to encrypt. If you stick the device into a USB port on its own, it won’t do anything, and the system won't detect it, because the Cipher USB FLE is set up with pass-through USB protocols. There has to be a drive on the other end.
The first time you attach it (and a required key drive) to a new PC, you will need to run the setup program and select a password. The device we tested was an F1, which required us to put a driver disk into the CD-ROM drive. You then set a password with the F1 the first time you set it up, which makes the encryption algorithm unique for that device. One set, you don’t have to remember the password anymore unless you want to change it, which is not recommended. The F2 models add a second layer of security – a password is required to decrypt files -- which is not present on the F1.
With the F1, the hardware itself is all you need to decrypt files, because it's using the same algorithm every time. As long as the F1 is attached to a computer, you can decrypt any file that was originally encrypted with the same F1 unit. The catch is that changing the password on the unit changes the algorithm. So if you encrypt a bunch of files with your Cipher USB FLE F1 unit while the password was set to "Pollyanna" and suddenly decide to change it to "OscarTango," you won't be able to decrypt the files from before. It would seem as if the password no longer matched, but in reality, you are using a different algorithm at that point. Hence the advice to never change the F1's password once you set it up the first time.
Once you know all those little quirks, the Cipher USB FLE works surprisingly well. We used one of the most generic USB drives we could find, a tiny 256M unit passed out at a trade show. We plugged it into the back of the F1 that was set up with the robust password of "test" (since password strength doesn't really matter). When the F1 was plugged into a computer running Windows 7, it detected both the key drive and the Cipher. We told it to open the key drive in one window and run the Cipher program from the F1 on the other. We then added a 5.49M test file to the key drive, which showed in the window and also on the status screen of the Cipher program. A quick right click on the file, and we were able to encrypt it. That process took less than two seconds, speeding along because the F1 uses its integrated hardware crypto engine instead of software to drive the process.
The key drive now contained the newly encrypted file, which surprisingly did not increase in size. It had the same name as before, and we could even tell that it was a bitmap. The only difference was that it now was listed as an Addonics file. It would not open, though Windows tried to get it to do so using photo viewing software, so the OS knew how it was supposed to work.
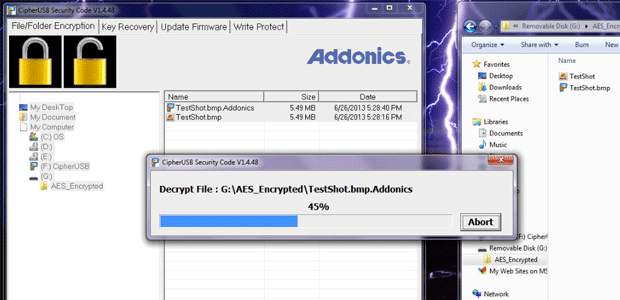
That actually brings up a bit of a concern. Since the name of the file and the file type are not hidden during the encryption process, a file called TopSecretAttackPlans written in Word will still be called that and identifiable as a Word file. While that would not give an attacker automatic access to the file, it would provide some clues. The file itself was protected using NIST-approved 256-bit AES encryption, so its likely unbreakable, though being able to see file names and types is still troubling.
For increased security, you can have the F1 encrypt an entire drive, though for maximum flexibility, just encrypting files as needed is better. Then you can work with your unsecured files as often as you need without having to run the drive through the F1. We would actually recommend setting up an encrypted folder within the drive and then leaving a text file outside of that window containing your contact information. That way a lost drive might make it back to you if found by an honest person, (I've personally returned three lost drives to their owners over the years) but still keep the data safe.
On the plus side, we learned that the Cipher USB FLE F1 is actually a bit of an encryption command center. Although you have to attach a key drive to the back of the unit to get it to run, you aren't limited to just putting encryption on that drive. You can encrypt any file or drive that is attached to the computer, even those on the host machine. In this way, the Cipher USB FLE F1 could be used to lock down an entire laptop or desktop PC, and it could be done relatively quickly and on the fly. You would just have to remember to keep the device close when you wanted to use the protected data, since it would be acting essentially as a token-based security system, though one that has native encryption.
The Cipher USB FLE F1 is a surprisingly inexpensive way to turn unsecured drives, which are essentially trash for a lot of government workers, into usable, protected stores of information. Using the F1 as a portable encryption command center makes even more sense, because it could be used anywhere to quickly protect data, or to unlock and work with data that had been protected with the same device -- or with an F1 that has the same password set-up. It's less magical when you peek behind the curtain, but no less impressive for ad hoc, easy-to-use security.





