Protecting systems from rogue root users


Connecting state and local government leaders
Hardware-based security can stop compromised credentials from being used to leak data.
Root users have elevated privileges on a network. They are responsible for upkeep of the systems by updating and installing new software or hardware. In a cloud infrastructure, a team of systems administrators typically has access to root credentials so they can make sure the cloud remains operational and delivers the performance agency users expect.
However, the privileges that allow root users to perform those legitimate operations may be misused. Whether by a disgruntled employee or an administrator who fell victim to social engineering or phishing attacks, root credentials can be exploited to compromise critical government applications.
The reason compromised root users are so problematic for security organizations is because they control the operating system, and the operating system controls all the applications running on the system. But once a system has been "rooted," all bets are off. A malicious root user can identify and disable software sensors to hide his trail; move laterally; steal valuable personally identifiable information, trade secrets or health data; or simply bug the system.
Root users' unsurpassed power to peek into any applications running on the system can be traced to how computer architecture has evolved. Computing today is based on a hierarchical trust model where the hardware and system software such as the BIOS have the highest privilege, followed by the hypervisor or virtual machine monitor (VMM), then the operating system and finally the applications.
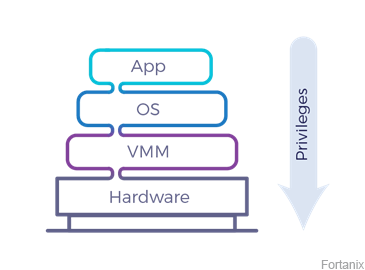
This model also means the applications have no protection or privacy from the underlying OS, which can fully control and inspect all processes on the system -- including inspecting or modifying a program's binary code, inspecting or modifying its data (including stored data, in-memory data, network traffic and encryption keys) and launching new processes that look like old processes. Similarly, the hypervisor has full control over the OS it runs and, by extension, the processes run by the OS. This access extends to the machine's all-powerful administrator or root user.
Roots can be compromised by a malicious insider, social engineering or even coercion. Enterprises today operate in multiple clouds across the globe under friendly and not-so-friendly government regimes. Some of those regimes might force the cloud provider to divulge root credentials. Once a root credential has been compromised, all software running on the systems, whether on-premises or on public clouds, is also readily compromised because of the strict hierarchical privilege model. Examples of potentially compromised applications include software key vaults, build servers, load balancers and code repositories.
Solving this security nightmare depends on taking advantage of the most privileged component in the computing architecture: the hardware, which is even more powerful than the OS and VMM. By leveraging trusted hardware, one can protect applications without relying on the intermediate OS. Fortunately, there has been a tremendous amount of progress in the field of trusted computing. Intel Software Guard Extensions (SGX), which help application developers protect certain code and data from disclosure or modification, is present in a majority of x86 clients and servers.
New solutions can protect applications in the presence of a compromised OS or VMM. They can keep applications encrypted even during runtime so that all their code and data remain secure, bypassing the traditional hierarchical privilege model.
Such an approach keeps applications binary and data encrypted, even during runtime, using the instructions provided by the CPU. This security architecture understands that the OS and hypervisor will not always be cooperative; it’s built for situations in which they have been compromised by malicious insiders. The runtime encryption keeps applications encrypted using hardware, bypassing potentially vulnerable software. Users get cryptographic certainty that even with a compromised OS and hypervisor, applications remain completely secure.
Encryption during runtime, working in conjunction with Intel SGX, ensures that the code and data of the application are only accessible by the application. The OS and hypervisor are needed to keep the system running, but they don't play a role in the security and privacy of information.
It is hard to overstate the benefits this solution brings to the secure operation of the enterprise. Compromised systems administrator credentials will no longer lead to leaked customer data. Agencies can run sensitive applications in public and remote clouds without compromising security and privacy. Applications can run in the most challenging geographic locations under unfriendly governments with full hardware protection.
Such hardware-based security ensures that disgruntled employees are unable to take treasure troves of information with them before they leave an organization. Cloud providers will no longer be able to view and alter data in the cloud, broadening the acceptable use of cloud computing to much larger parts of the organization.
Hardware-based security can change the way we think about securing enterprise systems.
NEXT STORY: IRS uses tech to track bitcoin transactions




