10 ways states can avoid becoming ransomware victims


Connecting state and local government leaders
Identifying the vulnerabilities that pose the most imminent threat and have the capability to cause widespread damage can make patching both practical and sustainable.
Over the past year, the U.S. has witnessed an unprecedented rise in ransomware attacks, with state and local governments bearing the brunt of the damage. In fact, recent RiskSense analysis shows that at least two-thirds of U.S. states have suffered a ransomware attack in the past 18 months. This makes it more important than ever to understand the factors driving this spike in government-focused ransomware, the unique challenges government agencies face and what they can do to better protect themselves.
The economics of ransomware
Ransomware has a very different financial model than most other cyber threats, and its unique approach is one of the main reasons government agencies are suddenly in the crosshairs of attackers. Financially motivated attackers have historically focused on stealing high-value data that can be resold on the black market -- such as payment card information, banking information, trade secrets and a variety of personal information. This strategy has made banks, retailers, and enterprises the most common targets and, consequently, the most likely to invest in security. By contrast, smaller government agencies were often not prime targets.
Ransomware attackers, however, don’t need a victim’s data to be valuable on the black market. They just need the data to be valuable to the victim. In fact, attacks that cause the most disruption to services are typically the most prized, making government networks ideal targets.
State agencies have proved to be relatively soft targets for attackers. Security teams in state and local agencies are continually underfunded. In some states, only 1% of agencies’ cash-strapped IT budgets goes to cybersecurity. Understaffed and underequipped, state and local leaders are quickly trying to adapt, as a recent survey of state CIOs found that security and risk management were the top priorities for 2019. And while leaders hope for larger budgets in the future, the simple fact is that state and local security teams will continue to be asked to do more with less. This makes efficiency and smart use of resources and staff time an even bigger priority than it is in traditional enterprises.
Smaller number of ransomware vulnerabilities cause most damage. A recent Spotlight Report by our security research team analyzed some of the most destructive strains of ransomware and the vulnerabilities they rely on to cause damage. While the study focused on families of ransomware that target enterprises as well as state and local governments, the findings exposed some common threads across both government and commercial organizations:
Old vulnerabilities cause big damage. The study found 16 vulnerabilities from 2015 or earlier that are still being used in ransomware attacks in the wild. This includes specific vulnerabilities in JBoss servers from 2010 (CVE-2010-0738) as well as Java vulnerabilities from 2012 (CVE-2012-1723, CVE-2012-0507). JBoss and Java vulnerabilities are heavily used by SamSam, which was behind many of the most notorious strikes, including the 2018 hit on Atlanta as well as attacks on school libraries.
EternalBlue remains an eternal problem. While not quite as old as the JBoss vulnerabilities, the MS17-010 vulnerabilities that fueled the WannaCry outbreak continue to wreak havoc today. These "wormable" SMB (server message block) vulnerabilities allow an attack on a single infected device to quickly spread throughout an organization. They continue to be used by the latest ransomware such as Ryuk, which was responsible for the recent attack on Lake City, Fla. Analysis from ESET has shown that the EternalBlue exploit that targets these vulnerabilities is actually on the rise, with a major spike in use beginning in April 2019. Clearly, even two years after WannaCry, many organizations have not patched.
So how can understaffed state and local IT teams keep pace with the rising tide of vulnerabilities, especially when some of the most dangerous vulnerabilities are old or may have low CVSS scores? To answer this question, we wanted to see if we could boil the tens of thousands of vulnerabilities down to a manageable number that government IT staff could realistically patch.
We focused on the 48 vulnerabilities that are actively being exploited the most by ransomware in the wild. We then further prioritized those vulnerabilities based on whether they are wormable, used by multiple families of ransomware or impact multiple products.
Here’s the ransomware top 10 list:
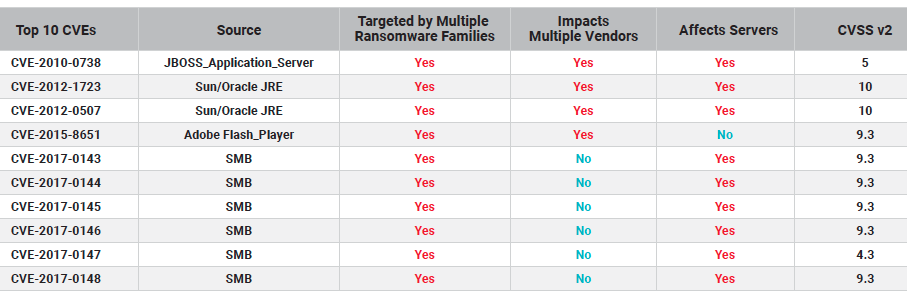
Click here for a larger size.
These findings illustrate that state and local government agencies will benefit more from pursuing a smarter, not necessarily a higher volume, patching strategy. With limited resources, identifying those vulnerabilities that pose the most imminent threat and have the capability to cause widespread damage and affect more than one software product used by an agency can make patching both practical and sustainable. While no single security measure is a cure-all, risk-based prioritization gives state, local and educational agencies a fighting chance against ransomware.




