Protecting workloads from sophisticated supply chain attacks

True runtime protection can determine, within milliseconds, if the code currently being executed by the workload came from the software developer or from an attacker.
According to a recent Canalys report, in 2020, more than 100 billion confidential data records were breached. This number points to an alarming trend since it exceeds the total number of records breached in the last 15 years. A root cause analysis of this trend has pointed to three urgent operational shortcomings that led up to these breaches:
- Poor security training.
- Improperly configured security controls.
- Security controls that lack contextual visibility.
While impacted government agencies can take remediate the first two shortcomings, there is very little that they can do to protect their infosec assets if they continue to deploy inadequate security controls. The recent SolarWinds, Kaseya, Hafnium and PrintNightmare attacks have exposed current imprecise and insufficient security controls that have contributed to the explosive growth in the number and sophistication of attacks.
To better understand what federal agencies can do to be better protected, it is imperative to first dig into the cyber kill chain that sophisticated attackers leverage.
Understanding the cyber kill chain
The kill chain starts with the attacker finding and targeting a server workload that operationalizes some software that has a vulnerability that has either not been patched or is undisclosed. A “workload” is typically any software or application that runs on a server, which houses the crown jewels of organizations. An unaddressed vulnerability can open the door for attackers to sneak into the memory subsystem of the victim’s software and persist for as long as they want. Attackers in the memory subsystem are far more dangerous than those having a presence on the disk. The bad actor can gain full keyboard control of the workload and can execute arbitrary code of their choosing -- not only on the infiltrated server workload but also on adjacent server workloads.
As part of the kill chain, bad actors:
- Send an exploit payload that includes enough malware to establish remote connectivity back to the attacker.
- Gain execution control by either manipulating critical pointers in the memory of compiled code or by having the application itself generate code unintentionally.
- Execute the attacker-controlled (malicious) code buried in the payload.
- Use the remote connectivity to drop and execute even more malware on the server workload.
- Execute the new malicious code on the workload to achieve their ulterior objectives.
How can agencies protect themselves?
To block the attacker from gaining the ability to execute arbitrary malicious code, agencies must deploy security controls that offer true runtime protection. Such a cybersecurity control can establish, within milliseconds, if the code currently being executed by the workload came from the software developer or from an attacker.
What is true runtime protection for server workloads?
Many host-based security controls such as enterprise detection and response (EDR) and host intrusion prevention systems (HIPS) claim they offer runtime protection. That may be true, in letter, but definitely not in spirit. In modern sophisticated ransomware, supply chain and data exfiltration attacks, the attacker targets either a known-and-unpatched or an unknown vulnerability in an application. Unless the true runtime security control can spot in real time, in milliseconds, when a vulnernability is being exploited, it is not a true runtime protection solution.
The graphic below shows data’s logical journey as it makes its way from the attacker to the victim. In a successful attack, the attacker starts by dispatching a maliciously crafted payload that traverses the network and ultimately lands at an application for final processing. As the application processes the malicious payload, the vulnerability causes attacker-influenced code to start executing.
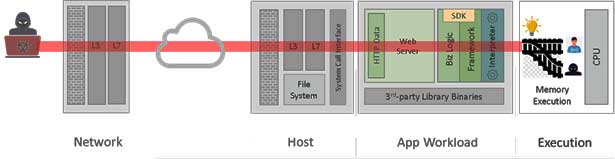
Image created by Satya Gupta, Virsec
Network-based security controls such as intrusion prevention systems, web application firewall and host-based security controls such as EDR, HIPS and antivirus are at a huge disadvantage in spotting when the victim server workload starts executing attacker-influenced code. Being so far away from the execution pipeline in the server workload, these tools do not have enough context to determine precisely when the code execution pieline has jumped the guardrails and started executing the attacker-influenced code.
Bad actors have realized that the current crop of security controls attempt to detect malicious code execution via either static signatures, threat feeds, behavioral anomalies or using event patterns recognized by the tool’s artificial intelligence and machine learning algorithms. A small tweak in technique is all it takes to bypass today’s controls.
With true runtime protection, an attacker can send any data to the application but cannot influence the code that is running on the server. By leveraging a knowledge base that is extracted directly from the application itself, it takes away the attacker’s ability to bypass the security controls. True runtime protection security controls cannot be undermined by attackers. By executing protection in real time, agencies avoid cyber disaster.





