Why Cybersecurity Awareness Month should be every month

Medesulda via Getty Images
COMMENTARY | Cybercrime costs have surpassed $10 trillion globally, illustrating the relentless threat and why state CISOs say they want the spotlight on cybersecurity year-round.
It’s that time of year again: Cybersecurity Awareness Month. A time when conferences, summits, webinars and cybersecurity articles converge to remind everyone how vital personal and institutional cyber hygiene is. After all, cybersecurity is an all-hands effort. So why then are so many chief information security officers frustrated by all the attention and cyber focus October brings?
Cyber threats to public institutions have never been more significant or pernicious, and they are continuous, 24/7. CISOs are constantly on guard and need their employees to similarly always to be cyber aware. Having a once-a-year focus is admirable, but what about the other eleven months? CISOs struggle to make cyber awareness a 24/7 mindset throughout the organization. They would much prefer cyber awareness campaigns that are permanent and engaging.
Cyber Awareness Month was first launched in October 2004 by the U.S. Department of Homeland Security and the National Cyber Security Alliance. In its early years, the campaign primarily focused on promoting basic cybersecurity practices, like regularly updating passwords and antivirus software. Over time, as the digital landscape and cyber threats evolved, the campaign has expanded its messaging to include more complex issues like phishing, ransomware and multifactor authentication.
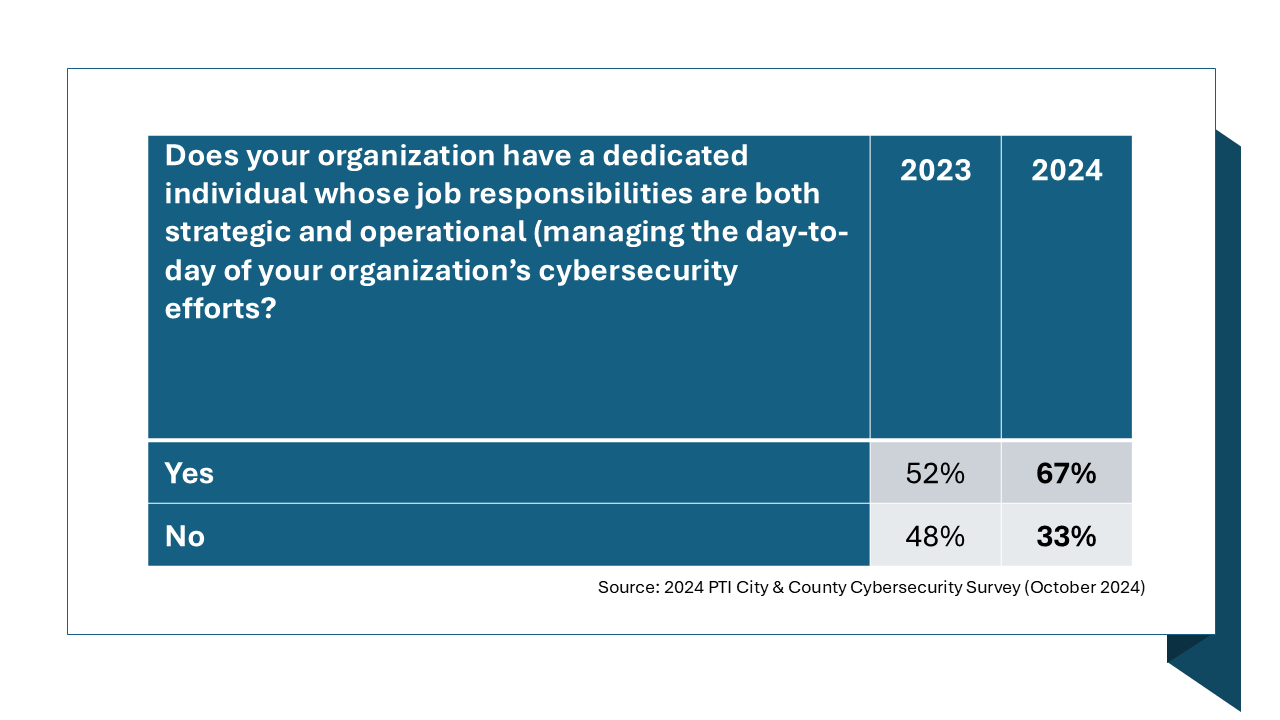
Now, it might be time for the awareness campaign to evolve yet again—much as the CISO role has in local government. According to a soon-to-be-published annual survey conducted by the Public Technology Institute, or PTI, where I am executive director, the CISO role or its equivalent is growing yearly. The 2024 report shows that 67% of respondents from a national sample had a dedicated, full-time professional overseeing their government’s cybersecurity.
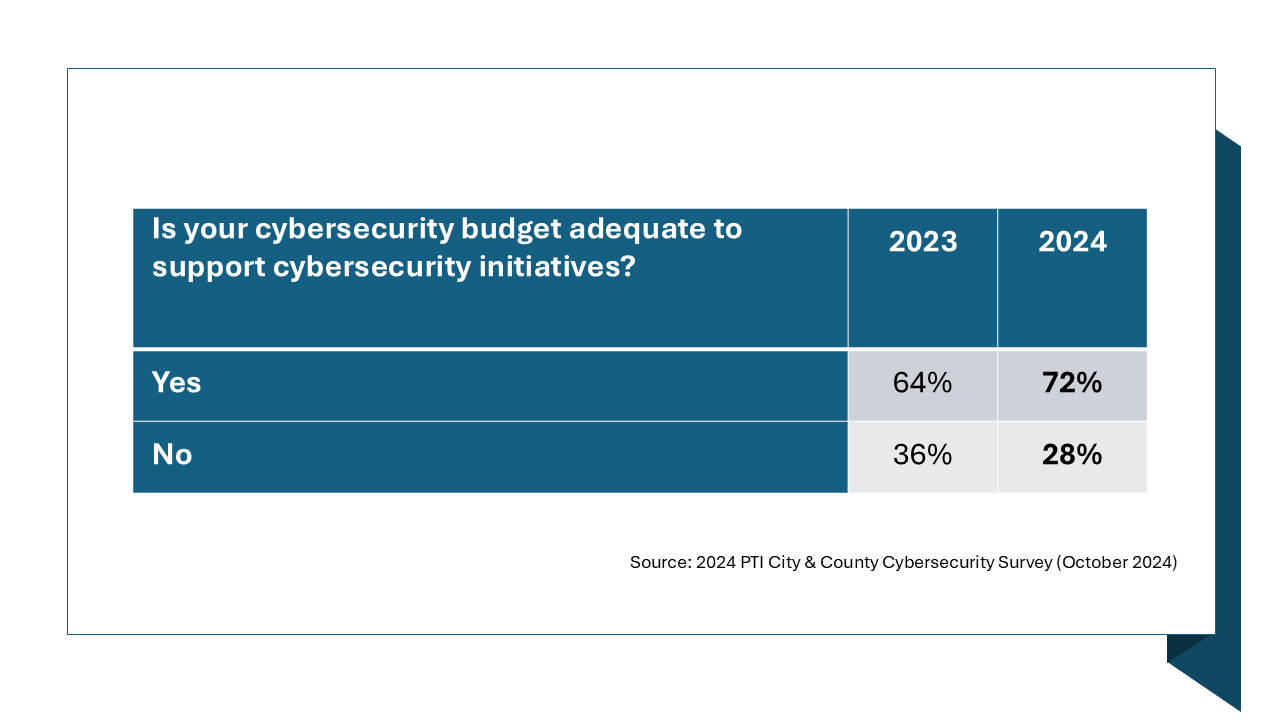
The survey asked local governments a range of questions, including one about funding. Cybersecurity funding has been a consistent concern for CISOs. But the responses this year are encouraging, with 72% of local governments saying “yes” when asked if funding was adequate. The 28% that answered “no” tended to be small local governments that typically lack the resources and leadership. While this category is tracking lower than in previous years, it is a reminder that not all local governments have the necessary resources to protect their citizens from cyberattacks.
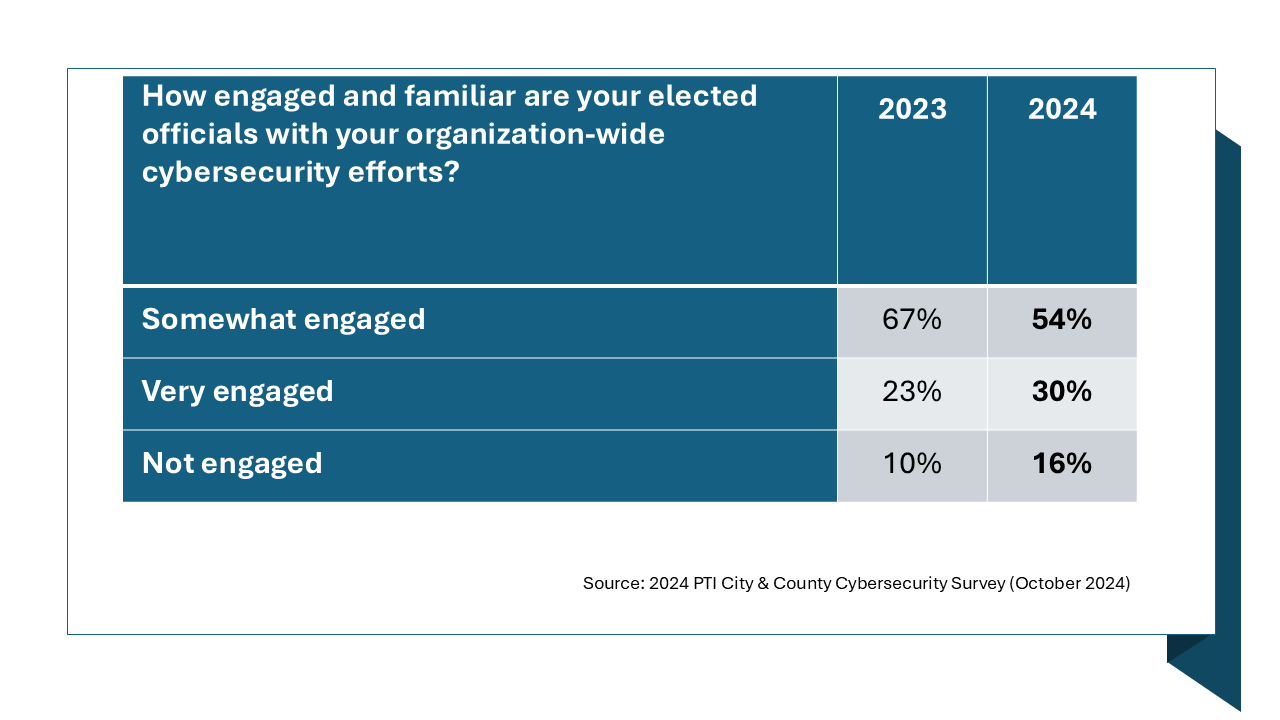
Finding fiscal support is essential, but political support from elected leaders may be as important. PTI has been tracking elected leader involvement for years, and this latest study reveals that while “very engaged” rose by 7%, the “not engaged” category grew by 6%, and the “somewhat engaged” declined by 13%.
Elected leaders are the ones who ultimately approve local government budgets and set overall direction. Most cyber experts argue that elected leaders should be very engaged by asking the right questions and ensuring their governance and operations are well-protected, as are citizen records and sensitive information. At the very least, they should set examples of good digital hygiene for all.
Fiscal support and support from elected leaders will continue to be crucial as cybercriminals are deploying new techniques every day that are becoming harder to detect.
In 2021, for example, the cybersecurity community awoke to a significant cyberattack caused by a breach in SolarWinds, a company that develops software for businesses to help manage their networks, systems and information technology infrastructure. At the time, a “supply chain” attack, in which cybercriminals gain access to unsuspecting customer systems by infiltrating a trusted supplier’s routine update, was new. Microsoft’s president said back then, “This was the largest and most sophisticated attack ever.”
As our dependence on technology grows, so do our vulnerabilities. This past July, a faulty update from CrowdStrike, an endpoint cybersecurity company, caused a massive IT outage that affected millions of Windows systems globally. Airlines saw major disruptions, 911 systems experienced outages, and many state and local government websites and computers went down. The episode has been referred to as a “single point of failure.” While everyone seemed. This latest incident has caused many IT professionals to rethink and evaluate where there may be single points of failure and how alternative systems could mitigate such a future emergency.
Now, 2024 presents even more significant challenges with the growth of AI tools. While local governments are increasingly turning towards this new technology, so are cybercriminals. Experts believe cybercriminals will soon be deploying AI-powered cyberattacks and intrusions.
So, Cybersecurity Awareness Month is an excellent time to reevaluate all things cyber. It’s a good time to review and practice various scenarios and plan accordingly. It’s also an excellent time to renew one’s commitment to proper cyber practices and awareness, extending that toward the other eleven months.
Dr. Alan R. Shark is the executive director of the Public Technology Institute and associate professor for the Schar School of Policy and Government, George Mason University, where he is also an affiliate faculty member at the Center for Advancing Human-Machine Partnership. Shark is a National Academy of Public Administration fellow and co-chair of the Standing Panel on Technology Leadership. Shark also hosts the bi-monthly podcast Sharkbytes.net. Dr. Shark acknowledges collaboration with generative AI in developing certain materials.






 By
By