3 ways to destroy data without taking it to Mount Doom
There are some myths about data destruction, but making sure information can't be retrieved from a hard drive isn't that hard.
Trying to destroy government data on a hard drive can sometimes seem like an epic Tolkien-created quest to destroy the One Ring. And there are just as many myths, legends and untruths surrounding the processes, too, to give many an IT hobbit nightmares. What if not all the data is removed? Can someone bring those files back to life? Will it be my reputation on the line if something happens?
The truth is that destroying data is easier than most people think. Let’s look at three reliable methods.
1. Brute force
Back when I was a kid, my father worked at the National Institute of Standards and Technology, and one of his jobs was occasionally destroying computer equipment that was being tossed out. Admittedly, this was done more to protect government purchasing discounts — not letting computers bought cheaply make it to the secondary market — than for security reasons. But for the most part, the effect was the same.
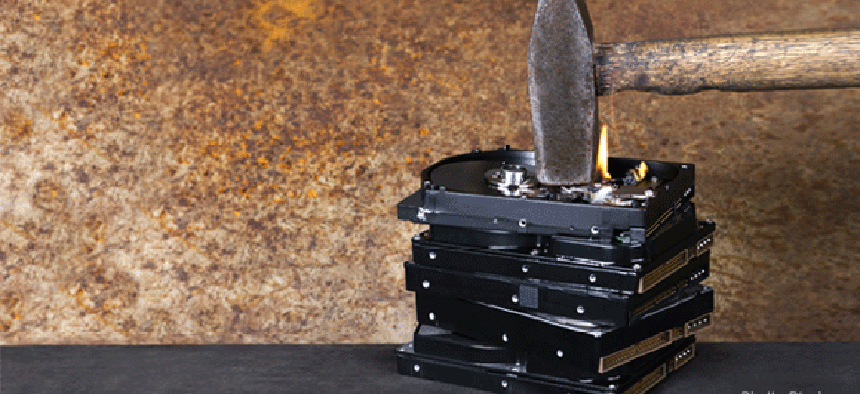
I was fortunate enough to be visiting him on one of those disposal days and got to help out. The required uniform was a pair of laboratory safety goggles. The only tool was a 12-pound sledge hammer.
I was thinking about that day I spent smashing government property after seeing an interview on Slashdot with Russell Chozick of Flashback Data, an Austin, Texas, based company that recovers data from hard drives. Chozick talked at length about all the different types of problems that drives experienced, where data was still recoverable. Everything from prolonged submersion in salt water from Hurricane Katrina to drives that were sent to a landfill, buried and bent in half, still had usable data, he said.
So what works to ensure that all data is destroyed on a drive that is no longer needed? Apparently, the sledge hammer method still works fine, but Chozick warns that it depends on the type of drive. A laptop drive with glass platters can be utterly destroyed by slamming it down hard onto concrete. But a desktop drive is more robust and really has to be smashed to pieces to prevent any type of recovery. Data also can be scraped off the platter, apparently, though that seems like a lot of work. Who wants to scrape when you can hammer?
2. Clean sweep
GCN has looked at various software products that can also be employed for this task. The latest one was WipeDrive 7, which even allows for remote destruction of data.
A common method, and one we use at GCN, is to use the code string “0xF6, 0x00, 0xFF, random, 0x00, 0xFF, random” to put a bunch of useless data on top of anything that is already sitting there when a drive is retired.
The government requires most agencies to go a bit further, using a seven-pass method where data is rewritten seven times according to the DOD 5220.22-M standard for the handling of classified information. But even that requires some interpretation of the documents to make sure you are doing it right.
Now, some might say that the "Gutmann" method requires 35 passes to be truly secure, but that is one of those myths that developed around the destruction of data over the years. The 1996 paper by Peter Gutmann has been all but disproved. And it was theoretical to begin with.
Gutmann said that some organizations (read: government entities) using magnetic force microscopy and scanning tunneling microscopy techniques might be able to tell if an original byte was a one or a zero. “Might” being the key word. Only with 35 passes could a drive truly be considered clean, he said. With no other information and no studies at the time, Gutmann was taken at his word and the 35-pass theory became gospel in government.
Even if it could be done at the time — and I have my doubts — today's high-density drives make magnetic force microscopic wizardry all but impossible to practice, something Gutmann himself recently stated. In fact, most drives these days can be considered secure after only a single pass from wiping software. The difference between a single pass and 35 can be hours or even days, depending on the type of drive and the size, so it's important to know the truth about this. A three-pass method should put everyone's mind at ease.
3. Magnetic method
Another method that can be used for extreme cases is degaussing, which bombards the drive with a magnetic field, similar to the EMP blast from a nuclear explosion. Devices like the new DataGauss machine from Data Devices International are a good example how degaussing has made it to the tabletop.
One theory said that degaussing didn't work with flash media, which was somehow protected from the process. Perhaps in the past some data could have survived, but machines like the DataGauss are certified today to destroy anything put in them, including flash media.
The one downside about degaussing a disk is that it can never be used again, even for new data. Its servo motor is almost always fried in the process.
So to be really secure, perform some type of software wipe, then degauss the disk, then smash it with a hammer. But let's not get too carried away. It's not the One Ring and it doesn't have to be tossed into the fires of Mount Doom to be destroyed completely. Any of the three methods here, a three-pass software wipe (or seven if it’s required for classified data), degaussing or a good smashing with a hammer will destroy your precious data.





