NIST draws up a security architecture for cloud computing

Connecting state and local government leaders
The agency has released a draft of a cloud security architecture intended to provide the security needed to speed government adoption of cloud computing.
Federal agencies are under orders to begin migrating applications to a cloud computing environment under a the administration’s cloud-first initiative, and the National Institute of Standards and Technology is developing standards and guidelines to enable the transition.
The latest document in that effort, a draft Cloud Computing Security Reference Architecture, Special Publication 500-299, lays out a risk-based approach of establishing responsibilities for implementing necessary security controls throughout the cloud life cycle.
This security reference architecture draws on and supplements a number of other NIST publications to provide the security needed to speed adoption of cloud computing.
This document supplements SP 500-292, Cloud Computing Reference Architecture. The security reference architecture provides “a comprehensive formal model to serve as security overlay to the architecture” in SP 500-292.
The draft publication describes a methodology for applying the Risk Management Framework described in SP 800-37, Guide for Applying the Risk Management Framework to Federal Information Systems: A Security Life Cycle Approach, adapted for the cloud. The formal model and security components in the draft are derived from the Cloud Security Alliance’s Trusted Cloud Initiative - Reference Architecture.
The Federal Risk and Authorization Management Program (FedRAMP) provides a baseline security authorization for cloud service providers, but agencies still are responsible for ensuring that security for resources moved to the cloud meets regulatory requirements. According to the document, “the ultimate objective ... is to demystify the process of describing, identifying, categorizing, analyzing and selecting cloud-based services,” for agencies trying to determine which cloud offerings best address their needs and best supports their business and mission-critical processes and services.
Complying with regulatory and security requirements in a cloud environment depends on the service and deployment model adopted by the agency, the cloud architecture, what resources are deployed and how they are managed. In addition to traditional IT security considerations, the publication also addresses cloud-specific characteristics, including:
- Broad network access
- Decreased visibility and control by consumers
- Dynamic system boundaries and mingled responsibilities of consumer and provider
- Multi-tenancy
- Data residency
- Measured service
- Significant increase in scale, dynamics and complexity of the environment
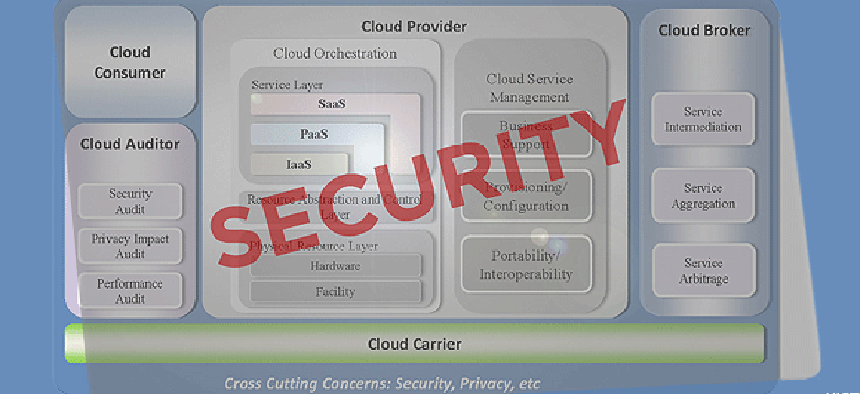
The architecture looks at the three primary cloud service models: software as a service (SaaS), platform as a service (PaaS) and infrastructure as a service (IaaS), and it addresses the roles of the various actors in the cloud environment: the consumer, provider, broker, carrier and auditor. The level of involvement for each actor in implementing security components is considered for each environment.
The document includes a case study of a typical cloud migration for a comprehensive messaging system that includes e-mail, calendar and document sharing. The case study focuses on the public cloud model because it offers examples of all the security components, but the methodology also is applicable to other models, including private, community or hybrid clouds.
Comments on the draft publication should be sent by July 12 to Michaela Iorga at Michaela.iorga@nist.go, using the template for comments and with "Comments SP 500-299" in the subject line.




