What 700 TB of cyber threat data can do for you

Connecting state and local government leaders
IBM’s cloud-based X-Force Exchange fosters sharing of cyber threat intelligence among contributing organizations.
The value of cyber threat intelligence increases as it’s shared.
That’s the idea behind the X-Force Exchange, a 700-terabyte platform of aggregated cyber threat information IBM has built to foster cybersecurity collaboration. This hoard of cybercrime data features IBM’s security intelligence research, a global network of third-party threat data, expert analyses and real-time insight on live attacks, all on a social sharing site built on IBM's cloud.
As the sophistication of cybercrime increases, governments and private organizations alike depend on sharing their threat intelligence. “The need for trusted threat intelligence is greater than ever, as 80 percent of cyber attacks are driven by highly organized crime rings in which data, tools and expertise are widely shared,” IBM said, citing a 2013 UNODC Comprehensive Study on Cybercrime.
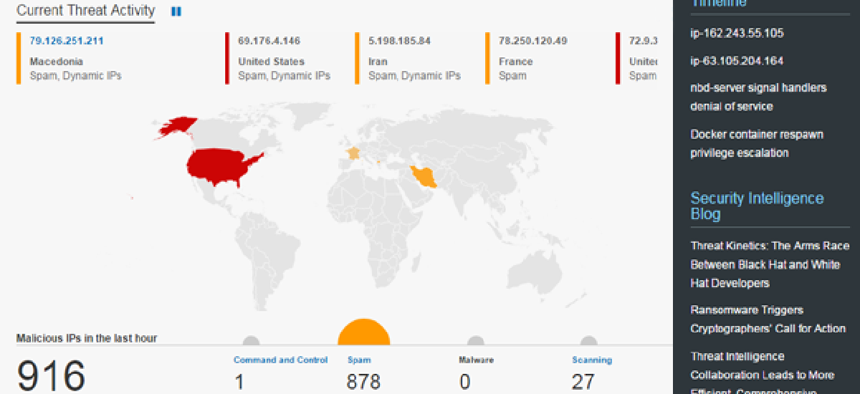
IBM has described the X-Force Exchange as “one of the largest and most complete catalogs of vulnerabilities in the world.” In detail, the platform will pull from threat data and intelligence based on more than 15 billion security events a day, over 25 billion web pages, more than 8 million spam and phishing attacks, a malware threat intelligence network of 270 million endpoints and reputation stats on a million malicious IP addresses that are categorized by geo-location and severity, the company said.
The cloud will continuously be updated -- it can add 1,000 malicious indicators each hour -- and as the third-party user base grows, so too will the depth of information, IBM said. Users can work with industry peers, analysts, researchers and trusted technology on a social interface with clearly organized tools, annotated findings and prioritized information. A library of application programming interfaces even works as an open forum for programmatic queries between businesses, machines and applications for further threat-fighting support.
In some ways, the platform looks like any other community social sharing site. Logged-in users can search, comment, collect and share information, while guests can view and search reports.
In the “activity” section, users can access recent vulnerabilities, find links to security intelligence blogs for helpful tips and search through trending topics and recent history of the entire community. In a personalized collections tab, users can add reports and pull in evidence from external resources, made shareable to the community or kept private.




